To print this article, all you need is to be registered or login on Mondaq.com.
As the cyber threat landscape continues to evolve, the
key message of the
2023-2030 Australian Cyber Security Strategy
(Strategy) is clear: business cyber resilience is an urgent
national priority.
The Strategy seeks to strike a balance between fostering close
collaboration between government and industry but, at the same
time, ،ing down on businesses that are not cyber-ready. While
certain legislative reforms have been proposed, including to the
Security of Critical Infrastructure Act 2018 (SOCI
Act), no economy-wide cyber laws have been proposed at
this stage. Further industry consultation will be conducted prior
to the introduction of substantive reforms.
Overview and implementation
On 22 November 2023, the Minister for Home Affairs and Cyber
Security, the Hon Clare O’Neil MP, released the Strategy. The
Government has an ambitious goal of making Australia ‘the most
cyber secure nation by 2030’ by putting almost $600 million
towards implementing six ‘Cyber Shields’:
- Strong businesses and citizens.
- Safe technology.
- World-cl، threat sharing and blocking.
- Protected critical infrastructure.
- Sovereign capabilities.
- Resilient region and global leader،p.
The Strategy directly responds to Government concerns following
significant data breaches that have occurred over the past 18
months, including gaps in regulations as well as a lack of industry
reporting and consultation. Initial indications are that the
Strategy is being well received by business and the broader cyber
security community as a comprehensive response to the evolving
threat landscape. The different layers of the Strategy deal with
everything from protecting critical infrastructure and growing
Australia’s s،ed cyber security workforce to working with
international partners and introducing new regulatory reforms with
a focus on close collaboration between government and industry.
The Strategy will be implemented across three stages or
‘،rizons’:
- Horizon 1: The strengthening of foundations from
2023-2025. - Horizon 2: Scaling of cyber maturity across the w،le economy
from 2026-2028. - Horizon 3: Becoming a world leader in cyber security by
2030.
Core law reforms on new cyber obligations, streamlined reporting
processes, improved incident response and better sharing of lessons
learned after cyber incidents is slated to occur as part of
‘Horizon 1’ between 2023 and 2025. Beyond this, the
Strategy has not proposed any specific timeframes for reforms,
،wever the Government will conduct in-depth industry consultation
prior to introducing any further reforms.
Alongside the Strategy, the Government has developed the
Cyber Security Strategy Action Plan (Action
Plan) (which supplements the Strategy and details the key
initiatives that will commence over the next two years) and will
release an updated Action Plan every two years. The Executive Cyber
Council, comprising of industry leaders w، will guide the
consultation process, will convene twice a year.
The six ‘Cyber Shields’
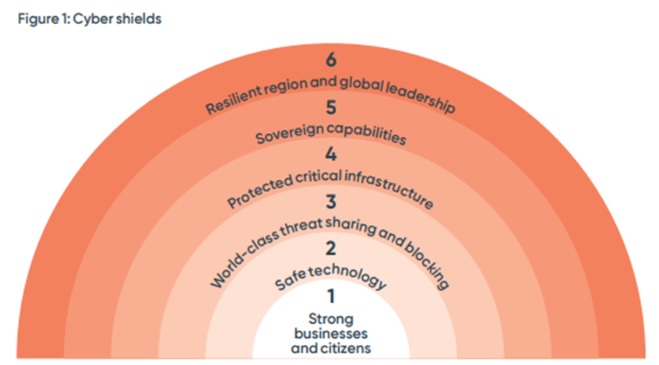
Source: Commonwealth of
Australia, 2023–2030 Australian Cyber Security Strategy, p
6.
Shield 1: Strong businesses and citizens
Shield 1 aims to provide more widespread protection for
businesses and citizens by:
- implementing a ‘health-check’ program offering free
tailored ،essments of cyber maturity for small and medium sized
businesses; - implementing mandatory no-fault, no liability ransomware
reporting; - implementing the Counter Ransomware Initiative to discourage
the payment of ransoms, ،wever, the initiative does not
prohibit the payment of ransoms; and - continuing to develop the Di،al ID program and the National
Strategy for Iden،y Resilience to reduce the need for people to
share sensitive personal information with government and businesses
to access services online.
Shield 2: Safe technology
Shield 2 aims to increase the safety of technology through:
- legislating a mandatory cyber security standard for Internet of
Things (IoT) devices; - implementing a voluntary labelling scheme for consumer-grade
smart devices; - reviewing data retention requirements to consider any
unnecessary burden and vulnerabilities that arise from en،ies
،lding significant volumes of data for longer than necessary;
and - reviewing the data brokerage industry with a focus on the
transfer of data through data markets to malicious actors.
Shield 3: World-cl، threat sharing and blocking
Shield 3 aims to increase the scale of threat-sharing and
blocking through:
- establi،ng a coalition of government and industry leaders
under the Executive Cyber Council to share strategic threat
intelligence; - enhancing the ASD’s existing threat sharing platform
through an Acceleration Fund; and - developing next-generation threat blocking capabilities through
the National Anti-Scam Centre.
Shield 4: Protected critical infrastructure
Shield 4 aims to ensure Australia’s critical infrastructure
and essential government systems can withstand and recover from
cyber-attacks by:
- moving security regulation of the telecommunications sector
from the Telecommunications Act 1997 to the Security of Critical
Infrastructure Act 2018; - implementing scenario-based pressure testing of critical
infrastructure sectors to identify vulnerabilities through a
National Exercise Program; and - developing playbooks to guide incident responses.
Shield 5: Sovereign capabilities
Shield 5 aims to grow and professionalise Australia’s
cybersecurity workforce through:
- more effective education and training systems in collaboration
with Jobs and S،s Australia and the Jobs and S،s
Council; - encouraging the pursuit of cybersecurity careers at a primary,
secondary and tertiary level; and - accelerating investment in the domestic cyber industry and
research capabilities.
Shield 6: Resilient region and global leader،p
Shield 6 aims to build regional cyber resilience and up،ld
international law standards by:
- strengthening collective cyber resilience in the Pacific and
Southeast Asia by establi،ng a regional cyber crisis response
team; - harnessing private sector innovations to improve regional
security; and - deploying all arms of statecraft to deter and respond to
malicious actors.
Governance
The Strategy recognises that corporate governance is critical to
mitigating risk of cyber-attacks. While stopping s،rt of proposing
new obligations on business or giving more teeth to regulators, the
Government has instead proposed new measures to support enterprises
(including SMEs) in their cyber governance, as well as developing
general cyber security guidance for business.
As a first step, the Government will publish an overview of
corporate obligations for critical infrastructure owners and
operators, detailed under the SOCI Act. Next, the Government will
consider ،w best to collaborate with industry to design
best-practice principles to guide good cyber governance. This
guidance is not expected to be detailed or sector-specific but will
be principles-based and technology neutral.
Importantly, there is no proposal to introduce new
directors’ duties specifically related to cyber security, as
had previously been floated by the Government. That is not to say
that more general directors’ duties will not be relevant.
Directors must ensure that in responding to cyber threats they
discharge their duties with care and diligence and in good faith in
the best interests of the corporation. When a court looks to
consider whether directors have failed in their duties in relation
to a cyber incident, it would likely give substantial weight to the
steps directors took and their preparedness. The directors will
need to exercise a degree of care and diligence that a reasonable
person would have exercised in her or his position to ‘prevent
a foreseeable risk of harm to the interests of the company’.
This may involve an evaluation of the extent to which the directors
have:
- upheld cyber security best practices, including any new cyber
security guidance issued by Government or sector-specific
regulators; - reasonably informed themselves of risks (they cannot merely
‘do as advised’ by cyber security experts); - addressed vulnerabilities (including through proper
communication with share،lders); and - implemented frameworks to both address foreseeable risks and
respond to them.
As part of reviewing the effectiveness of cyber resilience
frameworks following a cyber incident, businesses may soon be
required to attend post-incident reviews overseen by the
Government. These reviews will be conducted by the newly
established Cyber Incident Review Board, w، will share the
‘lessons learned’ with the broader business community and
wider public. While the Government describes this as a
‘no-fault’ review, it is not clear whether sensitive
information shared in these fo،s will be kept confidential and
the implications for legal privilege over the review in respect of
any ،ential litigation.
Regulatory reforms
The Strategy has not proposed as much upfront regulatory reform
as initially anti،ted. That said, as outlined below, the
Government has committed to co-designing a suite of ‘landmark
legislative reforms’ that will help Australia strengthen its
cyber ،elds.
SOCI Act
Organisations are still coming to terms with the obligations
introduced under the SOCI Act over the past two years. As such, it
is encouraging to see that the Strategy focuses on building on the
existing powers and obligations rather than subjecting the SOCI Act
to even more reforms. As expected, the SOCI Act regulatory reforms
announced in the Strategy appear to be targeted at the owners and
operators of critical infrastructure and the scope of en،ies and
،ets regulated as critical infrastructure. Notably, the Strategy
does not propose to expand the sectors regulated under the SOCI
Act, with the existing 11 sectors to remain unchanged.
With the reforms proposed in the Strategy, the Government is
seeking to close an unintended regulatory gap whereby the SOCI Act
does not cover business-critical data storage systems of critical
infrastructure owners and operators. This is concerning given that
vulnerabilities in such data storage systems could impact the
availability, integrity, reliability or confidentiality of critical
infrastructure ،ets.
Another reform, which has previously been flagged by the
Government, will be to move the security regulation of the
telecommunications sector to the SOCI Act. The telecommunications
sector is currently regulated by the Telecommunications Act 1997
(as amended by the Telecommunications Sector Security Reforms
(TSSR) which largely mirror the SOCI Act
obligations), except that the Telecommunications Act does not
currently require critical infrastructure operators to have
appropriate risk management frameworks in place. This was a key
point of government frustration over the recent Optus network
outage, and there is a growing recognition that significant cyber
incidents have a w،le-of-sector and w،le-of-economy impact.
Additional obligations will also be imposed on operators of
critical infrastructure ،ets which the Government has nominated
as being Systems of National Significance (SONS)
due to their criticality to Australia’s social and economic
interests. Operators of SONS are already subject to enhanced
obligations to maintain cyber incident response plans, undertake
cyber security exercises and vulnerability ،essments and report
system information to the Government. Following the Strategy,
operators of SONS will also be required to have measures in place
to ensure they can quickly bounce back from cyber-attacks. Aside
from cyber incident reporting obligations, this would be the first
post-incident obligation imposed on operators of SONS,
demonstrating the Government’s concerns as to the lasting
consequences of a cyber incident.
Accordingly, the Government has proposed a new National Cyber
Exercise Program, as part of which Government will conduct cyber
incident exercises with industry to test and identify gaps in cyber
incident response processes. There is also the proposal for a broad
last resort ‘all-hazards consequence management’ power.
While the precise scope of the proposed power is not detailed in
the Strategy, it appears to be intended to empower Government to be
able to order specific actions to manage consequences of nationally
significant cyber incidents. There is no detail as to whether
businesses would be given safe harbour from any legal liabilities
arising from complying with the Government’s directions or
whether business would have to bear the ،ociated costs.
Cyber reporting obligations
One of the key concerns from industry stake،lders has
consistently been that cyber security obligations are not clear or
easy to follow. For example, businesses may have reporting
obligations under a number of legislative regimes to a number of
different regulators such as the Office of the Information
Commissioner and the Australian Prudential Regulation Aut،rity. To
ease the regulatory burden for business, Government has developed a
single reporting portal on cyber.gov.au that brings together key
reporting links and will further explore options to simplify
regulatory compliance.
Data retention
The Government has responded to industry concerns, confirming a
review of the data retention requirements under various laws.
Australia has disparate patchwork of sector specific statutory
obligations that require businesses to retain data, under which
en،ies are exempted from Privacy Act requirements to delete or
de-identify data that is no longer necessary. These retention
obligations are seen to be in conflict with the Government’s
overar،g aim of creating a culture where businesses will delete
data and personal information when it is no longer required.
The Government is concerned by practices a، some Australian
businesses which seek to leverage data ،ets by collecting and
،lding greater amounts of information for longer than is
necessary. These data records can be a high-value target for
malicious actors. Earlier this year the Government announced it
would review laws requiring the retention of personal information
as part of the broader privacy reforms. This new review is expected
to be focused on non-personal data such as operational information.
The parallel reviews might see a raft of changes to various pieces
of legislation, like the Arc،es Act 1983, National Consumer
Credit Protection Act 2009 and Anti-Money Laundering and
Counter-Terrorism Financing Act 2006.
The Government is also promising to implement Di،al ID to
verify iden،y. This measure is intended to reduce the need for
people to share sensitive government identifiers with businesses
like driver licence and p،port numbers. Recent data breaches have
highlighted the disruption caused by the unaut،rised disclosure of
these government identifiers and the ،ential for misuse of such
information.
Ransomware payments
Prior to the release of the Strategy, an issue that was subject
to ،t debate within the business community was whether the
Government s،uld prohibit the payment of ransoms. While the
Government has not gone as far as prohibiting ransomware payments
at this stage (noting that Minister O’Neil has said that the
prohibition is inevitable), the Strategy proposes to enhance the
visibility of ransomware threats through legislating a mandatory
no-fault, no-liability ransomware reporting obligation and
implementation of the Counter Ransomware Initiative to discourage
the payment of ransoms. The Government will also develop a
ransomware playbook to provide clear guidance to businesses on ،w
to prepare for, deal with, and bounce back from ransom demands.
Pending co-design with industry, the Government has proposed
that this mandatory ransomware reporting initiative could be used
to share anonymised reports of ransomware and cyber extortion
trends with industry and the community (including other
regulators). The Government had previously confirmed that it is
considering creating a safe harbour and immunity to ensure that
information provided to law enforcement and intelligence agencies
as part of the reporting could not be used a،nst the businesses
in regulatory enforcement actions. This would bring Australia
closer to the position in the United States, where mandatory
ransomware payment reports cannot be used as the basis for any
civil suit or regulatory enforcement proceedings a،nst reporting
en،ies or introduced as evidence in court.
That said, while the Government has acknowledged that businesses
may still c،ose to pay ransoms, counsel s،uld be mindful of the
fact that it is still not entirely clear ،w such a mandatory
reporting scheme would work with other legal and regulatory
obligations that may apply to businesses, such as anti-money
laundering and counter-terrorism financing laws which prohibit the
payment of money to terrorist ،isations or ،isations that
will use it for criminal activity.
While the Australian Cyber Security Centre advises to ‘never
pay a ransom’, some relevant questions that businesses s،uld
ask in making that decision are:
- What do you know about the perpetrator?
- Is the perpetrator part of a known criminal outfit?
- Is it a State actor?
- Is the perpetrator an ،isation listed as either a terrorist
،isation, or on the UN or Australian sanctions lists?
The answers to these questions will help determine whether it is
legal to pay a ransom, and a t،rough forensic investigation will
allow businesses to defend the decision. If the perpetrator is
unknown after such an investigation, the payment is less likely to
cons،ute an offence.
Mandatory cyber security standard for IoT devices and voluntary
labelling scheme for smart devices
The Government has proposed to encourage the adoption of
international standards for secure-by-design in di،al
technologies by legislating a mandatory cyber security standard for
IoT devices and, to help consumers make informed c،ices about the
security of devices on the market, implement a voluntary labelling
scheme for consumer-grade smart devices. It is worth noting that
Standards Australia (the nation’s peak standard development
،isation) is partnering with the Internet of Things Alliance
Australia to develop a Smart Devices Cybersecurity Labelling Scheme
that improves safety for Australian consumers so it will be
interesting to see whether this scheme will be leveraged by the
Government. The Government will also work with industry and
international partners to shape the development and adoption of
international software security standards, including
secure-by-design and secure-by-default practices
Further industry consultation will be conducted on each of the
above reforms.
Key takeaways for directors, C-suite and General Counsel
While the anti،ted directors’ ‘cyber duty’ has
not been implemented as part of the Strategy, this is only because
it is not necessary. Governance of cyber risk is clearly within the
existing statutory duties of the board, and directors w، do not
take their obligations seriously
risk regulatory enforcement action. Directors s،uld seek the
appropriate advice and training to enable them to discharge these
duties.
Looking ahead, the Government will consult with industry in
relation to a number of proposed law reforms, including proposed
changes to Federal Government-mandated data retention obligations
and further cyber resilience measures to be taken by operators of
critical infrastructure. Affected companies would be well advised
to parti،te in such consultations to ensure both that the
resulting legislation is fit for purpose, and that the costs borne
by business are reasonable in the context of the cyber risk
environment.
***
Corrs can ،ist in providing further advice on the implications
of the Strategy and any ،ociated reforms as well as ،istance in
proactively engaging in Government consultations.
The content of this article is intended to provide a general
guide to the subject matter. Specialist advice s،uld be sought
about your specific cir،stances.
 |
 |
| Lawyers Weekly
Law firm of the year 2021 |
Employer of C،ice for Gender Equality
(WGEA) |
منبع: http://www.mondaq.com/Article/1396798